Introduction
Last month, we published a piece taking a look at the digital goods supply chain, its overlaps with the real economic supply chain, and how tariffs affect that. A lot of it was predictive in nature. Anytime we get to predicting, we like to follow up to see how accurate our predictions have been. It’s only been a month since that post…so let’s call this a short-term reflection. We can check back later this year to see if it has aged any better.
Let’s break down some of our takes and possible signals for (or against) our case.
Cloud Provider Diversification
A major theme in our last piece was the idea of a resilient and diversified multi-cloud strategy, both in geography and cost structure. We identified a driver of this shift in thinking as “shifting geopolitical postures.” To check if our take is playing out, we’ll look at the top international cloud providers and their performance over the past couple of years. The question is: are users and organizations spending more on different (non-US) cloud providers than before the 2025 supply chain shocks?
For this analysis and data availability, we’ll discuss public companies. Here are some names and their recent market share performances since 2022:
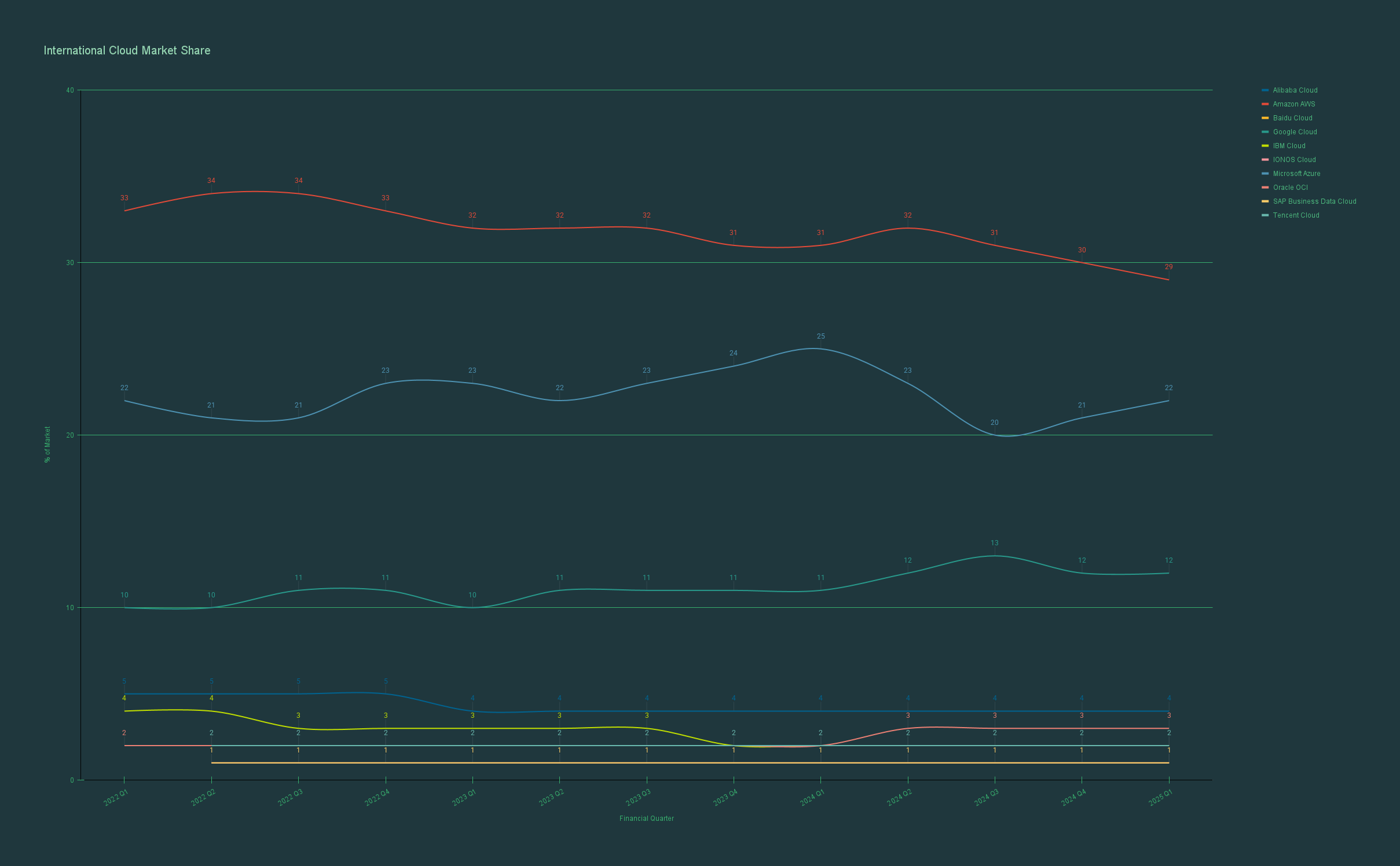
Insights and conclusions from the data:
US Providers had 68% market share in Q1 2025 (details below):
Amazon AWS: 29% (-2pp vs Q1 2024)
Microsoft Azure: 22% (-3pp vs Q1 2024)
Google Cloud: 12% (+1pp vs Q1 2024)
Oracle OCI: 3% (+1pp vs Q1 2024)
IBM Cloud: 2% (flat)
On the other hand, non-US providers had 9% market share in Q1 2025 (broken down below):
Chinese providers: Alibaba Cloud (4%), Tencent Cloud (2%), Baidu Cloud (1%) = 7% total
European providers: IONOS Cloud (1%), SAP Business Data Cloud (1%) = 2% total
The most significant trend is market share redistribution within US providers:
Losers: AWS (-6.5%) and Azure (-12.0%) lost a combined five percentage points
Winners: Google Cloud (+9.1%) and Oracle (+50.0%) gained share
Non-US stability: All non-US providers remained flat, showing no momentum
If we were to characterize this time span into distinct periods:
Q1-Q2 2022: Non-US share doubled from 5% to 10% - the most significant geographic shift in the dataset
2023-2025: Non-US share plateaued around 9%, showing no sustained growth toward geographic diversification
No 2025 supply chain shock impact: Despite expectations, no acceleration in non-US adoption is visible (yet)
Key Findings
Peak diversification occurred in 2022, not in response to 2025 supply chain shocks
Chinese providers (the most logical geopolitical hedge) have been flat at 7% for three years
European alternatives remain minimal at 2% combined market share
Internal US competition seems to be the dominant force, not geographic diversification
Verdict: Our prediction that shifting geopolitical postures would drive geographic cloud diversification is wrong....(for now)*
*I’ll defend us a bit here. A broad and slow-burning prediction like the rotation out of the modern hyperscaler ecosystem won’t take effect after only a couple of months. Executives don’t make infrastructure decisions that quickly, and most enterprises’ IT budget allocations move glacially compared to other market signals. The data reveals the market made its primary geographic adjustment in 2022 and has focused on optimizing within the US provider ecosystem. Organizations seeking resilience appear to have chosen multi-US provider strategies over geographic diversification prior to 2025. Let’s see how these numbers change in the next couple of years.
Dependency Management as a Core Business Function
The other major trend and prediction we discussed in the last piece can be loosely translated from the above buzzwords to, “digital work needs inventory management, and it should be taken seriously.” Basically, start running risk management, business impact analysis, and due diligence for the digital supply chain, not just the physical. The follow-up will highlight incidents that prove this. I believe MBAs may call these “case studies.” Anyway, here are some fun (?*) stories:
New Vulnerability Just Dropped: a public study (linked here: https://arxiv.org/pdf/2406.10279 ) found a new attack vector in the age of AI: package squatting (alternatively: slopsquat). In relatively simple terms, this is a new technique in which hostile actors to exploit generative models’ tendency to “hallucinate” (see: make sh*t up) and add non-existent packages into someone’s codebase when prompted to refactor or edit code. This can result in code that doesn’t compile or fails locally. However, when done in our wonderfully complex and interconnected world wide web, this ends up with someone maliciously creating this package, adding some sort of malware, and letting the generative models do the rest. As a computer science PhD and researcher noted to Ars Technica, “if a user trusts the LLM’s output and installs the package without carefully verifying it, the attacker’s payload, hidden in the malicious package, would be executed on the user’s system.”
Who Watches The Watchers: last year, the infamous XZ Utils backdoor vulnerability was discovered. Security researcher Alex Stamos noted that it “could have been the most widespread and effective backdoor ever planted in any software product.” Basically, a maintainer of the open source XZ Utils compression library, who had spent almost two years gaining trust, slipped a remote-access backdoor into versions 5.6.0 and 5.6.1 of the library. Fedora, Debian testing, AlmaLinux and others briefly shipped the tainted builds before a Microsoft engineer caught the anomaly while debugging sluggish SSH traffic. Essentially, anyone linking the poisoned liblzma could have handed attackers shell access, compromising the organization.
Happy Anniversary CrowdStrike: it’s been almost a year since a memory read issue in one vendor’s codebase almost brought down the global economy (or slowed it down significantly). We covered it in depth here (https://sitebolts.com/crowdstrike-incident/), but to echo our own work, we mentioned two key insights back then that appear to be ringing true today:
No system is an island: Modern software is an increasingly complex wave of interlocking parts, integrated solutions, and 3rd party dependencies. We are all interconnected between the different libraries, packages, and APIs that hold up our systems. This means someone’s sloppy internal processes around software updates can turn into your nightmare. IT teams should create a comprehensive map of their enterprise architecture and identify potential points of failure where their systems interact with external ones, especially ones with privileged access. This includes understanding the nature of updates at these intersections. Does your vendor do silent updates? Can you choose when to update? Is it automatic? Knowing the answers to these questions can be the difference between a gracefully handled change or weeks of downtime (aka loss of business)
“Build, buy, or partner” can be a life or death decision: Most technologists and IT folks are constantly playing the game, “should I build this myself, buy it from someone else, or partner with someone to get it done?” This game might not seem like a critical business moment when you’re choosing between CRM plugins or API providers, but as this incident has shown, someone choosing CrowdStrike over a competitor or the native Windows EDR service was the difference between an organization having a normal day or bleeding millions. It’s impossible to treat every decision as a life or death call, but leaders (both technical and nontechnical) would do well to place more weight on moments that require setting down foundations for “load bearing systems” (hint: if you use computers for anything in your business, you will have many of these moments). After all, every complex system starts as a simple one that transforms a little more after each subsequent change. It is crucial to have people making decisions with these dimensions of risk in mind, even from Day 1.
“We’re All Looking For The Guy Who Did This”: The White House released an executive order earlier this year mandating an update to agencies to improve software security standards, protect government networks, leverage AI for defense, and clarify cybersecurity rules. If only that were the only role the executive branch was playing in today’s environment.
The Lawyers Always Win: In 2023, Cybersecurity Ventures predicted that the global annual cost of software supply chain attacks to businesses will reach a staggering $138 billion by 2031. On top of that, regulators are increasingly indicating that ultimate accountability for cyber risk management rests with the board of a company. This can mean that board members can be held personally liable for major cybersecurity breaches. With these potential damages and regulatory shift, board members that used to ignore security discussions might be taking a bit more of an active interest in this area of the business. In fact, perhaps these board members will insist on managing digital dependencies with the focus and granularity applied to risk management in other parts of the (physical) business. Perhaps.
*I’m sure they weren’t fun for the relevant IT team they affected.
Verdict: Our prediction that technical dependencies can no longer remain strictly within engineering's domain is shaping up to be correct as organizations scramble to handle the risks in this new digital supply chain.
Conclusion
You win some, you lose some. When we posted our take on the digital supply chain last month, we certainly didn't expect our predictions and trend analysis to see immediate success (or failure). Again, we're talking about enterprises unwinding their previous IT policies and strategies. A global paradigm shift and rotation away from a purely US-based cloud and security strategy is not a story that unfolds in a couple of quarters. We'll revisit this. However, we're positive our predictions will play out over time as early signs support our analysis. Check back for Part 3 closer to year-end to see the shifts.
References
CRN. (2025). AWS, Microsoft, Google fight for $90 B Q4 2024 cloud market share. Retrieved May 27 2025, from https://www.crn.com/news/cloud/2025/aws-microsoft-google-fight-for-90b-q4-2024-cloud-market-share (CRN)
Cybersecurity & Infrastructure Security Agency. (2024, March 29). Reported supply chain compromise affecting XZ Utils data compression library (CVE-2024-3094). https://www.cisa.gov/news-events/alerts/2024/03/29/reported-supply-chain-compromise-affecting-xz-utils-data-compression-library-cve-2024-3094 (CISA)
Executive Office of the President. (2025, January 16). Executive Order 14144: Strengthening and promoting innovation in the nation’s cybersecurity. Federal Register. Retrieved May 27 2025, from https://www.federalregister.gov/documents/2025/01/17/2025-01470/strengthening-and-promoting-innovation-in-the-nations-cybersecurity (Federal Register)
Goodin, D. (2025, April 29). AI-generated code could be a disaster for the software supply chain—here’s why. Ars Technica. Retrieved May 27 2025, from https://arstechnica.com/security/2025/04/ai-generated-code-could-be-a-disaster-for-the-software-supply-chain-heres-why/ (Ars Technica)
SiteBolts. (2024, August 15). Unpacking the CrowdStrike incident: A deep dive into a global IT disruption. SiteBolts Blog. Retrieved May 27 2025, from https://sitebolts.com/crowdstrike-incident/ (sitebolts.com)
Spracklen, J., Wijewickrama, R., Sakib, A. H. M. N., Maiti, A., Viswanath, B., & Jadliwala, M. (2025, March 2 rev.). We have a package for you! A comprehensive analysis of package hallucinations by code-generating LLMs (Version 3) [Preprint]. arXiv. https://arxiv.org/abs/2406.10279 (arXiv)
Synergy Research Group. (2025, May 1). AI helps cloud market growth rate jump to almost 25 % in Q1. Retrieved May 27 2025, from https://www.srgresearch.com/articles/ai-helps-cloud-market-growth-rate-jump-back-to-almost-25-in-q1 (Synergy Research Group)
Wikipedia contributors. (2024, March 29). XZ Utils backdoor. In Wikipedia, The Free Encyclopedia. Retrieved May 27 2025, from https://en.wikipedia.org/wiki/XZ_Utils_backdoor (en.wikipedia.org)
